 a journal of interesting technical ideas . . .
a journal of interesting technical ideas . . .
SSH is a pretty well known protocol that’s used for a lot of different things. Most of us are familiar with the basics and a trick or two. This article is to try to consolidate a lot of the uses I have for SSH and share them. The article is a quick review of basic terminal access and banners. This is the first in a series, so more advanced topics are covered in succeeding posts.
SSH is included in modern operating systems. Apparently it can now also be installed on Windows (I’ve included a link). If you use Windows, the standard client suggested is PuTTY (I really like Solar-PuTTY as well). I have not used Windows as a client or server in my testing, so hopefully my comments will be helpful but I suspect server setup is going to be different.
My walk through assumes you are using a command-line client. Note that the ssh client is typically installed in the *nix world. If you want your box to be the server then you’ll need to add it via sudo apt install openssh-server (Debian/Ubuntu).
Most of us encounter SSH as a secure replacement for telnet. SSH allows us to connect to a remote terminal from the command line. Assuming that I wanted to connect to my firewall by it’s IP address and that there was an account named “brent” there, I can connect using _ssh username@Destination. If this is the first time you’ve connected, you’ll be asked to confirm the fingerprint.
brent@MintyTwenty:~$ ssh brent@192.168.24.230
The authenticity of host '192.168.24.230 (192.168.24.230)' can't be established.
ECDSA key fingerprint is SHA256:1XYZ12MBd5Sb345ABOBhoKx42D+STU56szGR/d3LkGs.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.24.230' (ECDSA) to the list of known hosts.
brent@192.168.24.230's password:
brent@inspiron:~$
The fingerprint is to protect against a man-in-the-middle attack, where your traffic is being re-directed to a malicious third party. Before you type in (and reveal) your password, best to make sure that this is a trusted server! So, where do we find the fingerprint to match it to? The easiest way to get it is to go to your server and use ssh to connect to itself: ssh username@127.0.0.1. This will show the local fingerprint. If someone has already used this trick and accepted the fingerprint, you can delete ~/.ssh/knownhosts (not recommended) or use ssh-keygen to examine the local public key.
brent@MintyTwenty:~$ __ssh-keygen -lf .ssh/id_rsa.pub
4096 SHA256:cjyCsHXYZ12dESNo+12AB/oGGaxY1JHSTU%1p3Aeouw brent@X (RSA)
SSH banners are specified in the ssh daemon configuration (/etc/sshd_config), To specify a banner, find the line reads “#banner none” and edit it to specify a file. The contents of this file will be displayed before the password prompt.
sudo nano /etc/sshd_config
banner /etc/banner.txt
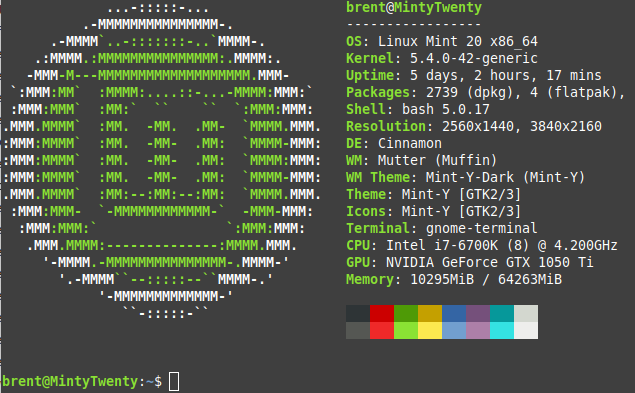
After authentication the prompt displays the server hostname. You can display a banner after authentication by editing ~/.bashrc. This has a side benefit - the terminal, when connected to locally or remotely, processes ~/.bashrc before it produces a prompt. Go to the end of that file and add whatever you like - that output will be displayed before a prompt is produced. I’ve listed some cool ideas to build a dynamic banner below.
sudo add-apt-repository ppa:dawidd0811/neofetch
sudo apt install neofetch
echo "neofetch" >> /home/brent/.bashrc # Add the command to the end of .bashrc

Figlet - draws letters in ASCII for a nice banner and any command can be piped through it (echo “for example” | figlet). It’s available in the standard Ubuntu repository.
Curl - pull in data from the web. Try curl v2.wttr.in/Hickory+NC. A more practical example might be:
curl wttr.in/Hickory+NC?format=2 # check out the github page for lots more options
data=$(sensors | grep "id 0:" | cut -c16-23) #sensors displays a lot of data.
# Grep just grabs the one line, and cut pulls temp out.
echo "CPU Temp:${data}"
Part two of this series will cover secure authentication options.